 Don't buy a database encryption product without extensive security features that are easy to use.
Don't buy a database encryption product without extensive security features that are easy to use.Encryption isn't enough. You need to guard against in-house threats with password protection and restricted access controls. A good encryption tool will let you audit all users that attempt to view your sensitive data.
Auditing Your Encrypted Data
Session Auditing records all attempts at encryption or decryption of your protected data. This information is valuable for reporting and/or tracing any unwanted access to encrypted data. Because usual read/write activity can be extensive, session auditing tracks distinct read and/or write operations against given columns for all user sessions that access encrypted data. For instance, if a user selects 1000 decrypted rows of sensitive data from an encrypted table, the Encryption Wizard will simply add one auditing record per column to report that a given user has decrypted that given column. If the user selects those rows again, the event will not be reported for the session – until the user logs out and then connects again, thus creating a new session.
Password Protect Your Data
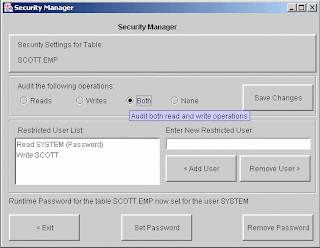
Runtime Passwords add a further layer of protection for your encrypted data. Runtime Passwords require users to validate a password before they can gain encryption and/or decryption privileges for a given schema, table, or column. There are two types of Runtime Passwords:
Default Runtime Passwords can be optionally assigned to a given database object, such as a schema, table or column. After the Default Runtime Password is defined, all users must authenticate the password before they can have access to the given database object protected.
This second type of Runtime Password works exclusively with Restricted User Lists as discussed in the previous section. Any user on a Restricted User List can be assigned a specific Runtime Password. These User-Specific Runtime Passwords, will of course take precedence over any Default Runtime Password assigned for a given database object.
Password protection insures that a malicious individual with DBA privileges cannot access any Oracle account and view encrypted data. Use this in conjunction with the Administrative Password to protect your encrypted data from malicious hacks into your Oracle RDBMS.
Restrict Users to Your Data
The Encryption Wizard allows you to define restricted user lists for any given schema, table, or column. A restricted user list instructs the Encryption Wizard to only grant those database accounts listed the ability to encrypt and/or decrypt data. You may also specify a Runtime Password that these users must supply before they can view encrypted data. This feature used in conjunction with password protection allows you to protect encrypted data even from a user with full DBA privileges.
Guarding against in-house threats is a must. Encryption keys can be stolen from the Oracle SGA, if you don't convert them like the Encryption Wizard does.
1 comment:
Very well explained. I am not having much idea about this important concept but after reading the above article I have understood what decrypted views are meant for. These views serves with multiple benefits and allows to view or change the encrypted data in an application.
sap support packs
Post a Comment