Free downloads now available to Oracle database customers:
http://www.relationalwizards.com/encrypt_pres/ewpres.html
Monday, June 1, 2009
Thursday, August 2, 2007
Data Encryption Software Should be Easy to Use

Oracle Database Security Using Intuitive Encryption Software.
What is database encryption? Simply, it is encrypting the actual physical data within your relational database. Encryption is the best way to guard against data-theft and the huge costs you incur when that happens. With a good encryption strategy, a data thief will be holding junk and not valuable corporate or government data.
A successful database encryption tool should be easy-to-use and intuitive. Managing encrypted data and migrated applications is more daunting than the actual Encryption Process and should be made as painless as possible.
Tools like the Encryption Wizard for Oracle allow you to secure your Oracle data without a headache. If your Encryption efforts are not point-and-click or intuitive, well what are you doing?
Download the Encryption Wizard today, and make Oracle security an attainable reality!
Download Page
Data Encryption Software Requires Power With a Slick Interface
 A Good Database Encryption Tool Will Automate Encryption at the Schema, Table or Column level.
A Good Database Encryption Tool Will Automate Encryption at the Schema, Table or Column level.Everyone, it seems, sells software out there with terrible user interfaces. A good database encryption tool should make your security efforts easier, not harder. Different applications require different levels of security.
Schema Level Encryption is the most powerful of the three levels of Encryption. When using Schema Level Encryption, all one must do is specify a schema by using a pick-list.
When we choose Schema Level Encryption, we are instructing the Encryption Wizard to encrypt all valid columns for that schema. Encryption of this type should not be performed until you are comfortable using the Encryption Wizard.
Schema encryption does not imply that your complete schema will always be encrypted. If new tables are added to your schema, the Encryption Wizard will not be aware of them unless you choose schema encryption again to protect the remaining tables.
When you choose to encrypt a single table without selecting any columns, the Encryption Wizard will, of course, attempt to encrypt every valid column within that table. As discussed in the features page, columns that are primary keys, unique keys, foreign keys, default values, and conditional constraints are skipped.
When employing Table Encryption, specify a schema and table name by using the two uppermost pick list that appears on the Encryption / Decryption screen. Choose both the schema owner and table name of the object that you want encrypted. After table encryption, all columns that appear on the right of the screen will be encrypted.
Column Level Encryption is the fine-grain level of encryption for the Encryption Wizard. With column encryption you specify and encrypt distinct column(s) only.
To define encryption at this level, first chose the table owner and table name from the two uppermost pick-lists that appear at the top of the Encryption / Decryption Screen. Once you have chosen the appropriate table to encrypt, simply click on those column(s) you wish to encrypt that appear in the column list on the right of screen.
A freindly and intuitive encryption interface allows your mind to remain focused on what is important:
Securing your valuable Oracle data.
Database Encryption Should Have Point and Click Management Screens
 Easy Management Tools Encourage Good Practices With Encryption.
Easy Management Tools Encourage Good Practices With Encryption.The real value of encryption software like the Encryption Wizard for Oracle is its easy-to-use and well-organized management features.
Notice that the Manage Encrypted Data Screen has a similar format to the Encryption Decryption Screen. You may manage encrypted data at the schema, table, or column level. To manage a given encrypted table - all we need to do is optionally select the schema owner and table name of the given object. Once we have selected chosen the table name from the two pick-lists, the Encryption Wizard will show us the encryption details for each column of our encrypted table. To highlight a column, simply click on the column name with your mouse.
Encrypting data and migrating applications to encrypted data sets is hard enough without being stuck without a good management tool to view and modify your encryption efforts.
Organized and Intuitive Security Management a Must for Oracle Database Encryption.
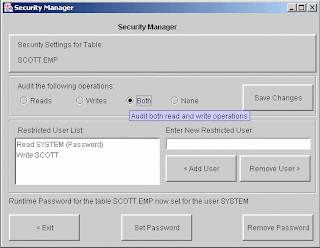 Don't buy a database encryption product without extensive security features that are easy to use.
Don't buy a database encryption product without extensive security features that are easy to use.Encryption isn't enough. You need to guard against in-house threats with password protection and restricted access controls. A good encryption tool will let you audit all users that attempt to view your sensitive data.
Auditing Your Encrypted Data
Session Auditing records all attempts at encryption or decryption of your protected data. This information is valuable for reporting and/or tracing any unwanted access to encrypted data. Because usual read/write activity can be extensive, session auditing tracks distinct read and/or write operations against given columns for all user sessions that access encrypted data. For instance, if a user selects 1000 decrypted rows of sensitive data from an encrypted table, the Encryption Wizard will simply add one auditing record per column to report that a given user has decrypted that given column. If the user selects those rows again, the event will not be reported for the session – until the user logs out and then connects again, thus creating a new session.
Password Protect Your Data
Runtime Passwords add a further layer of protection for your encrypted data. Runtime Passwords require users to validate a password before they can gain encryption and/or decryption privileges for a given schema, table, or column. There are two types of Runtime Passwords:
Default Runtime Passwords can be optionally assigned to a given database object, such as a schema, table or column. After the Default Runtime Password is defined, all users must authenticate the password before they can have access to the given database object protected.
This second type of Runtime Password works exclusively with Restricted User Lists as discussed in the previous section. Any user on a Restricted User List can be assigned a specific Runtime Password. These User-Specific Runtime Passwords, will of course take precedence over any Default Runtime Password assigned for a given database object.
Password protection insures that a malicious individual with DBA privileges cannot access any Oracle account and view encrypted data. Use this in conjunction with the Administrative Password to protect your encrypted data from malicious hacks into your Oracle RDBMS.
Restrict Users to Your Data
The Encryption Wizard allows you to define restricted user lists for any given schema, table, or column. A restricted user list instructs the Encryption Wizard to only grant those database accounts listed the ability to encrypt and/or decrypt data. You may also specify a Runtime Password that these users must supply before they can view encrypted data. This feature used in conjunction with password protection allows you to protect encrypted data even from a user with full DBA privileges.
Guarding against in-house threats is a must. Encryption keys can be stolen from the Oracle SGA, if you don't convert them like the Encryption Wizard does.
What are Decrypted Views?
 Decrypted Views allow users to see encrypted data as original table data, while the data is still encrypted.
Decrypted Views allow users to see encrypted data as original table data, while the data is still encrypted.To allow for applications to access physically encrypted data, the Encryption Wizard Administrator can optionally create decrypted views against any table with encrypted data.
Decrypted Views display data in unencrypted format, and thus allow applications to seamlessly read and/or write to the decrypted data objects through the use of an automatically generated instead-of database trigger created for each view. Decrypted views can be dynamically created and dropped at any time through the Encryption Wizard User Interface or the Encryption Wizard API.
Decrypted views are objects that appear as regular tables displaying original data to applications or users with the appropriate privileges.We can create decrypted views in any schema with the appropriate privileges to view the underlying encrypted base table.This will allow applications with the appropriate privileges to view or change encrypted data.
Why buy encryption software that doesn't automate this process?
Demand Key Backup and Recovery That is Intuitive and Fast
 Intuitive Key Backup and Recovery Allows Remote Key Storage at the Click of a Mouse.
Intuitive Key Backup and Recovery Allows Remote Key Storage at the Click of a Mouse.Key backup and recovery is vital for any encryption tool. You might want to store your keys on a floppy disk, so only when it inserted, can data be encrypted. Don't buy software that doesn't make backup and recovery a simple task. You have better things to do than manage encryption keys. Why pay money for a headache? You will need a simple interface in an emergency.
The Encryption Wizard for Oracle now offers complete or partial key backups to a flat-file.This will allow users to backup database encryption keys to removable disks and/or use removable disks as a requirement to read encrypted data. Notice the easy-to-use interface that manages both backup and recovery.
The Encryption Wizard also allows you to password protect your backups and insures that backups from one Oracle database cannot be loaded into another database. Because the Encryption Wizard performs another Triple DES round on these keys, it is not necessary to encrypt the backup file - unless you want another level of protection.
Subscribe to:
Comments (Atom)